-
 Solid state laser
Solid state laser
-
 Enantiomer
Enantiomer
-
 Water
Water
-
 Time
Time
-
 H.264
H.264
-
 Antipsychotic
Antipsychotic
-
 Cephalopod
Cephalopod
-
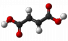 Fumarate
Fumarate
-
 African longfin eel
African longfin eel
-
 Hartley 2 comet
Hartley 2 comet
-
 GFP
GFP
-
 Statin
Statin
-
 Epileptic seizure
Epileptic seizure
-
 Ribonucleotide
Ribonucleotide
-
 Phytotherapy
Phytotherapy
-
 Metabolomics
Metabolomics
-
 Avogadro's law
Avogadro's law
-
 Ice shelf
Ice shelf
-
 Homo habilis
Homo habilis
-
 CGS system
CGS system
-
 Minamata Bay Disaster
Minamata Bay Disaster
-
 Green and blue framework
Green and blue framework
-
 Aplite
Aplite
-
 Time stamping
Time stamping
-
 Germinal
Germinal
-
 Instrumental aberration
Instrumental aberration
-
 Progesterone
Progesterone
-
 Resilient
Resilient
-
 Sub-addressing
Sub-addressing
-
 Algal film
Algal film
Asymmetric cryptography
In asymmetric cryptography, the algorithms are public but each individual has a pair of keys: one is secret allowing them to perform operations that they alone are supposed to be able to do (signature or decryption), while their public key is sent to allow their correspondents to perform the reciprocal operations (verification of the signature or encryption of the message). The two keys have "asymmetric" roles, hence the terminology.
One well known example is the RSA algorithm.
Latest
Fill out my online form.



