-
 Biotope
Biotope
-
 Internet Storm Center
Internet Storm Center
-
 Reflected light
Reflected light
-
 Furuncle
Furuncle
-
 Ramjet engine
Ramjet engine
-
 Dulong-Petit law
Dulong-Petit law
-
 Aerocapture
Aerocapture
-
 TWMD
TWMD
-
 Second
Second
-
 DHCP
DHCP
-
 Big Crunch
Big Crunch
-
 Metabolism
Metabolism
-
 Gavage
Gavage
-
 Cytology
Cytology
-
 Genomics
Genomics
-
 Ambulacra
Ambulacra
-
 RSPB
RSPB
-
 Exuvia
Exuvia
-
 Hox gene
Hox gene
-
 CD-ROM
CD-ROM
-
 Isotropic
Isotropic
-
 Melamine
Melamine
-
 Charadriiformes
Charadriiformes
-
 Class IV antiarrhythmic
Class IV antiarrhythmic
-
 Phytosociology
Phytosociology
-
 Lunar Reconnaissance Orbiter
Lunar Reconnaissance Orbiter
-
 Tourette's syndrome
Tourette's syndrome
-
 Photovoltaic solar energy
Photovoltaic solar energy
-
 Phenotype
Phenotype
-
 Helsinki Convention
Helsinki Convention
Man-in-the-middle attack
A man-in-the-middle attack is a computer hacking technique where encrypted exchanges between two people or two computers are intercepted to decode the messages. The attacker must therefore be able to receive the messages from both parties and to send responses to one party while passing themselves off for the other party.
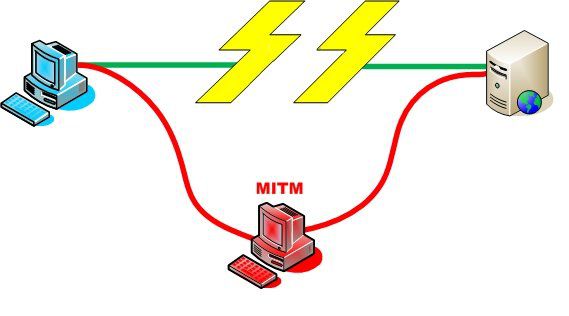 In a man-in-the-middle attack, (MITM for man-in-the-middle), a communication between two computers (here, a PC on the left and a server on the right) is intercepted by a third party, here MITM. The computer and the server appear to be conversing together, but all the messages actually transit via MITM which can read them and pass itself off as one of the two parties. © DR
In a man-in-the-middle attack, (MITM for man-in-the-middle), a communication between two computers (here, a PC on the left and a server on the right) is intercepted by a third party, here MITM. The computer and the server appear to be conversing together, but all the messages actually transit via MITM which can read them and pass itself off as one of the two parties. © DR
Latest
Fill out my online form.



